How To Bypass Skout Face Verification
The highlights
- The two methods of fooling confront verification: spoofing and bypassing
- Method one: Spoofing
- Method 2: Bypassing
- Tips on choosing hacker-resistant liveness
From phishing to deepfakes, identity theft is threatening businesses like never before. In 2019, one US company reportedly lost x million dollars afterward scammers fabricated an audio deepfake of the CEO requesting a money transfer.
One of the latest trends in identity fraud prevention is called 'liveness,' as well known as 'facial biometrics identification.' It allows businesses to ensure that the existent holder of a document is nowadays during verification. Many companies are switching from ID and selfie checks to liveness detection in pursuit of more than reliable onboarding processes.
Even so, different liveness solutions provide varying levels of security. Some of them merely protect against simple kinds of fraud, similar tricksters wearing newspaper masks; while others tin handle cunning hacks such as man-in-the-middle attacks.
At Sumsub, we've spent years testing out the various liveness technologies on the market. Today, we desire to share with you how tricksters bypass liveness and provide insights into choosing the best identity fraud protection.
The ii methods of fooling confront verification: spoofing and bypassing
When it comes to fooling facial biometrics, the oldest trick in the book is to vesture a mask. Indeed, fraudsters use silicone masks, printed photographs of other people, or even life-size mannequins to go onboarded or hack into accounts. This kind of fraud is known as 'face spoofing.'
The second method of tricking liveness is a bit more advanced. It involves fraudsters hacking into cameras and injecting pre-recorded videos or hacking the server itself and editing uploaded biometric data. This method is referred to as bypassing.
Run into Sumsub's liveness detection in action. Go a demo today.
Method ane: Spoofing
Chinese scholars recently discovered that Face ID, Apple's facial verification system, can be hands hacked by placing glasses—with two black dots taped in the middle—on the face of a sleeping device owner. Such a pull a fast one on unlocks Apple devices since Confront ID cannot thoroughly scan the eyes of a person wearing spectacles. This is i of the simplest spoofing techniques out there. Now let's accept a look at some more complex methods.
How fraudsters use pictures to spoof liveness
In the era of social media, fraudsters tin can obtain almost anyone'south picture and use information technology to fool face up verification. Therefore, if a liveness technology does non clarify the depth of an prototype, fraudsters can simply use social media images to hack devices and accounts.
This is indeed the case with the Samsung Galaxy S10'south confront recognition arrangement—which can be hands tricked past using someone'southward photo on a screen.
Fraudsters can likewise use a similar method to gain access to people's bank accounts, among other sensitive information.
Using video to fool liveness
In our manufacture, conventional wisdom states that if a liveness organisation asks users to make movements like winking or blinking, it becomes impossible to trick the system.
Unfortunately, these movements tin be recorded in advance, and some liveness systems fail to recognize these pre-recorded videos, as is the case with the USAA Bank.
Face spoofing with masks
Fraudsters can spoof liveness systems past using a wide range of props, from paper masks to life-size mannequins.
There are silicone masks then realistic that it is incommunicable to detect when a fraudster wears i. Criminals in fact used this loophole to impersonate the French Defence Minister and were able to steal $90 million. They did this by phoning heads-of-states, wealthy businessmen and large charities via Skype and challenge that they needed coin to save people kidnapped by terrorists.
Silicone masks can work if liveness technologies do not scan skin texture, blood flow, and the other characteristics of a real face.
Suggested video: 'Human confront or hyper-realistic mask? Tin can you tell the difference?' by the Academy of York
Using deepfakes to trick liveness
In 2018, a video in which Barack Obama called Donald Trump certain names went viral. The video was so realistic that many actually believed it. All the same, in reality, this was a deepfake.
Deepfakes are videos or audios that have been created using bogus intelligence. If initially deepfakes were used to cause harm to famous persons or just have a laugh with a friend, the evolution of this technology has led to companies being frightened that deepfakes could threaten their businesses.
Suggested video: Deepfakes: Is This Video Even Real? | NYT Opinion
Fraudsters are increasingly using deepfake engineering science to impersonate CEOs and steal money from corporations. In 2019, the Wall Street Journal reported that criminals had used AI-based software to deepfake the voice of a United kingdom of great britain and northern ireland CEO and stole $243,000 USD.
Deepfake technology can also be used to spoof or bypass liveness. Since everyone tin can create a deepfake at little to no cost, as there are many free deepfake generators, fraudsters tin hands face-swap with the individual they want to hack and gain admission to their account.
Method 2: Bypassing
Bypassing liveness does non involve impersonation. Instead, fraudsters hack the liveness system itself past swapping-in or editing biometric information.
Every liveness technology contains three weak points that hackers tin can target:
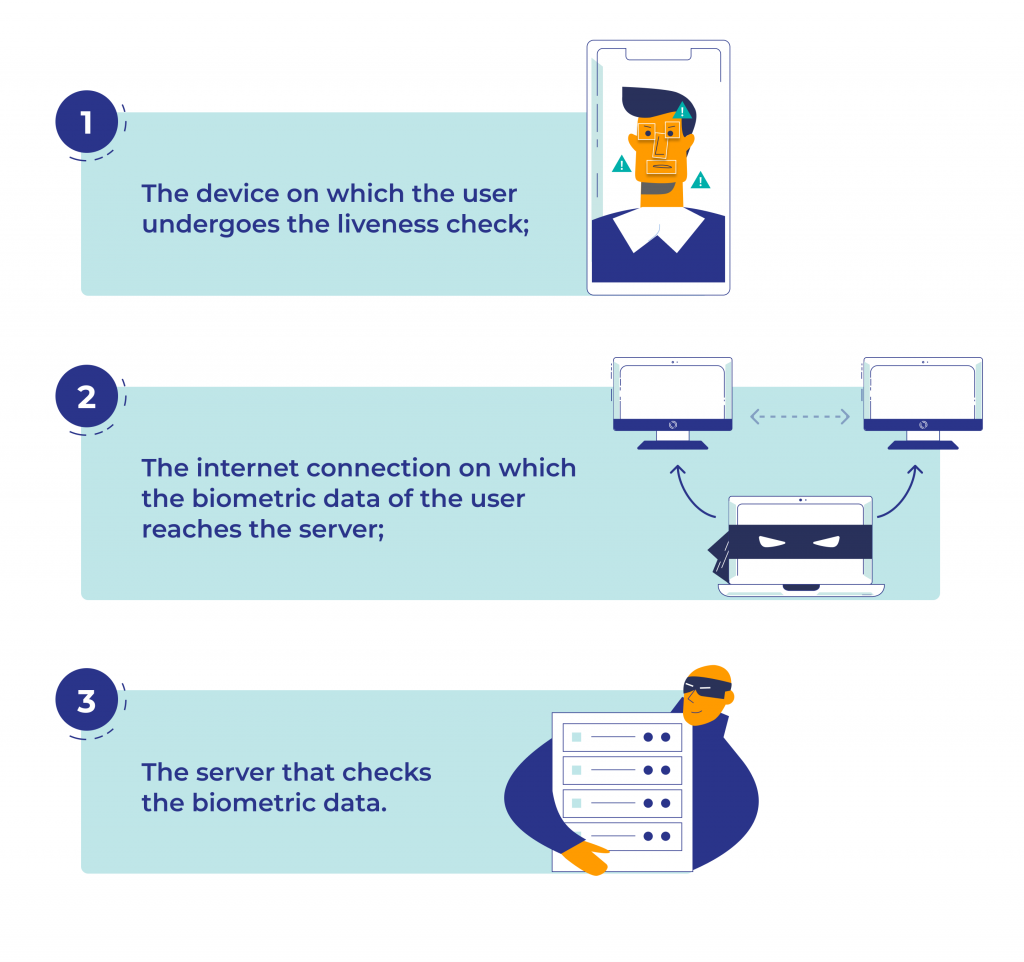
Fraudsters tin take over a phone camera and inject a pre-recorded video or deepfake. Data transmitted over the internet can also be intercepted if it is not encrypted properly, and a server tin be hacked.
Let's see how we can protect ourselves from spoofing and bypassing.
Want to implement face verification that provides the best security? Attempt out Sumsub'southward liveness detection solution.
Tips on choosing hacker-resistant liveness
When selecting a liveness solution, businesses should ensure that it protects against both spoofing and bypassing. Based on our experience of testing liveness solutions, nosotros've gained insights into choosing the most secure option.
Above all, liveness solutions should differentiate between real faces and artificial objects, like a mask or a screen. To do so, the solution must analyze parameters such every bit:
- Image depth;
- Eye reflections;
- Skin texture;
- Blood period.
Simply how can you tell if a solution really has the technology to examine these parameters? The only way to notice out is by testing the solution. Here is how:
- Present a static image to the system;
- Endeavor to pass the verification with your eyes closed;
- Use a face up-spoofing prop, such as a mask, a deepfake, or a video.
A reliable engineering should discover any of these fraudulent attempts.
It is also vital to inquire the liveness solution provider about the data encryption mechanisms that they employ. Their solution must provide state-of-the-art encryption that withstands invasions like replay or homo-in-the-middle attacks.
In essence, testing out a liveness technology by employing various spoofing and bypassing methods will ensure that you choose the nearly reliable choice.
Looking for liveness detection and face verification solutions? 'Prooface' keeps the perfect balance between maintaining high conversion rates and preventing fraud. Test it as many times as you similar and see for yourself.
Source: https://sumsub.com/blog/learn-how-fraudsters-can-bypass-your-facial-biometrics/

0 Response to "How To Bypass Skout Face Verification"
Post a Comment